15.12.2020 | Gregor Walter
Threat Analysis of the EKANS Ransomware - How Honda had to Stop Production

In June of this year, Honda had to shut down parts of its production at various locations due to a cyberattack. The attackers exploited known security vulnerabilities to gain access to the internal network and programmed the information they obtained into the ransomware. The malware was then distributed internally and encrypted selected files on the infected PCs that were necessary for production-specific processes. The domain controllers were spared, as the ransom note was stored on them. As a result, production had to be stopped for several days, which led to considerable damage. Honda has not commented on this incident to date.
In the following analysis, the procedure and consequences of the suspected perpetrator EKANS are examined in more detail.
EKANS is the name of a Windows ransomware that first appeared in December 2019. If you read the word from back to front, you get “SNAKE”, another ransomware with which EKANS is closely related and with which, for example, the German Fresenius Group was successfully attacked. Both EKANS and SNAKE belong to a family of ransomware that works by encrypting specific files. In contrast to SNAKE, EKANS specializes in industrial control systems (ICS).
On Sunday, June 7, 2020, an interruption of the computer network was detected at Honda. On the following Monday, parts of production in the USA, South America and India had to be stopped. On the same day, experts replaced the code of the malware that was presumably responsible for the outage at Honda.
Vulnerabilities in MS RDP or SMBleed were most likely used as entry points. Examination of the code revealed the hardcoded network name mds.honda.com and the corresponding hardcoded IP address 170.108.71.15, which is only accessible on the internal Honda network and cannot be accessed by the public. EKANS uses this information to ensure that the attack is only carried out in the attack victim’s network. EKANS is therefore specifically adapted to the company that is to be attacked.
After launching, it first checks whether the malware is located in the company network of the attack target. If this is the case, the Windows firewall is activated and network connections are cut. In the next step, a hard-coded “kill list” is used to identify and deactivate processes on the target machine. Files used by ICS are then encrypted. In the final step, the customer is asked to send money via a ransom note in order to receive the decryptor.
In connection with the absence of e.g. worm-like propagation mechanisms and components that establish connections to C2s, it can be assumed that the malware in the incident at Honda was distributed manually after the attackers had compromised large parts of the domain (they were able to execute code on DCs). According to Kaspersky’s ICS CERT, a script created in the Domain Policy Scripts folder in the SYSVOL directory, which was used to distribute the analyzed sample, was used for deployment at Honda.
The results of the triage as well as the static and dynamic analysis of this EKANS sample of the incident at Honda with the MD5 hash ED3C05BDE9F0EA0F1321355B03AC42D0 are shown here in simplified form as a flow chart:
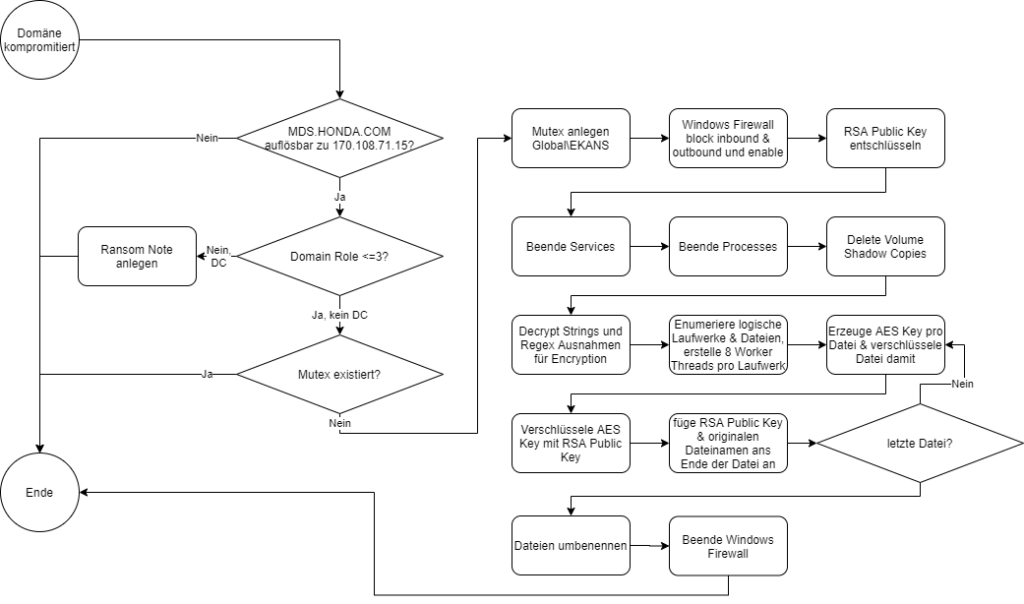
In the sample under consideration, the ransom note is only stored on domain controllers.
In the impact assessment, EKANS is examined based on the analysis in terms of business interruption, recovery time and loss of information, among other things. A scale was drawn up for the assessment, according to which EKANS must be classified as critical.
To minimize the risk, in addition to general measures such as backup, firewall, logging and monitoring, further measures such as sandboxing, DNS security, URL filtering and, from a certain criticality, intrusion detection and intrusion prevention systems as well as security operation centers are recommended.
EKANS is dangerous and expensive for affected companies. However, due to the manual distribution and target-specific adaptation, the global extent is low. Several incidents at well-known industrial companies such as Honda and BAPCO have caused a stir. In the case of Honda, the attackers were seen to have hardcoded the FQDN and IP, which involves a certain amount of effort. From this it can be concluded that such an elaborate attack is only worthwhile due to the financial strength of the company. EKANS shows a new development in ransomware that targets ICS-specific processes and systems. It can be assumed that this development will continue and that new functions will make other companies in the CRITIS sector, such as hospitals, power plants and public transport, targets for attacks.
Cybersecurity Risk Management Security Architecure

