01.03.2019 | Thomas Kessler
2-factor Authentication: Not Only Important for the EPR!

The EPDG requires two-factor authentication not only for patients, but also for healthcare professionals and their assistants. This article shows how this can be implemented using the resources available in the hospital or care home.
Identity theft is one of the major problems of information security: user accounts for online services that can be accessed from the Internet are subject to constant attacks by criminal individuals and organizations, and it has long been known that these attacks can be countered with strong authentication, as is commonly used in e-banking, for example. The implementing legislation for the Federal Act on the Electronic Patient Record (EPDG) therefore requires so-called two-factor authentication (2FA) for all persons accessing an electronic patient record.
However, the situation regarding access by healthcare professionals (HCPs) and auxiliary persons (HIPs) differs from that of patients: Not everything that a private individual can be expected to do when using an online service sporadically is also suitable for everyday clinical practice in a hospital or care home. At the same time, resources and infrastructures are available there that cannot be assumed for a private individual. Below we show what an EPDG-compliant 2FA could look like in a care home or hospital.
2 Factors: Where to get them from?
We use the term 2-factor authentication to describe procedures that combine a “having” factor with a “knowing” or “being” factor. The “having” factor is always required, which can be hardware (a smartcard, SIM card or other token) or software (e.g. an app). The “knowing” factor is usually a more or less secret password that is managed and checked centrally on a server or decentrally on a personal device; this is also known as a PIN or token PIN. Finally, the “being” factor is an individual physical feature such as a fingerprint or facial shape. There are various implementation options for all three factors and their combination (see illustration).
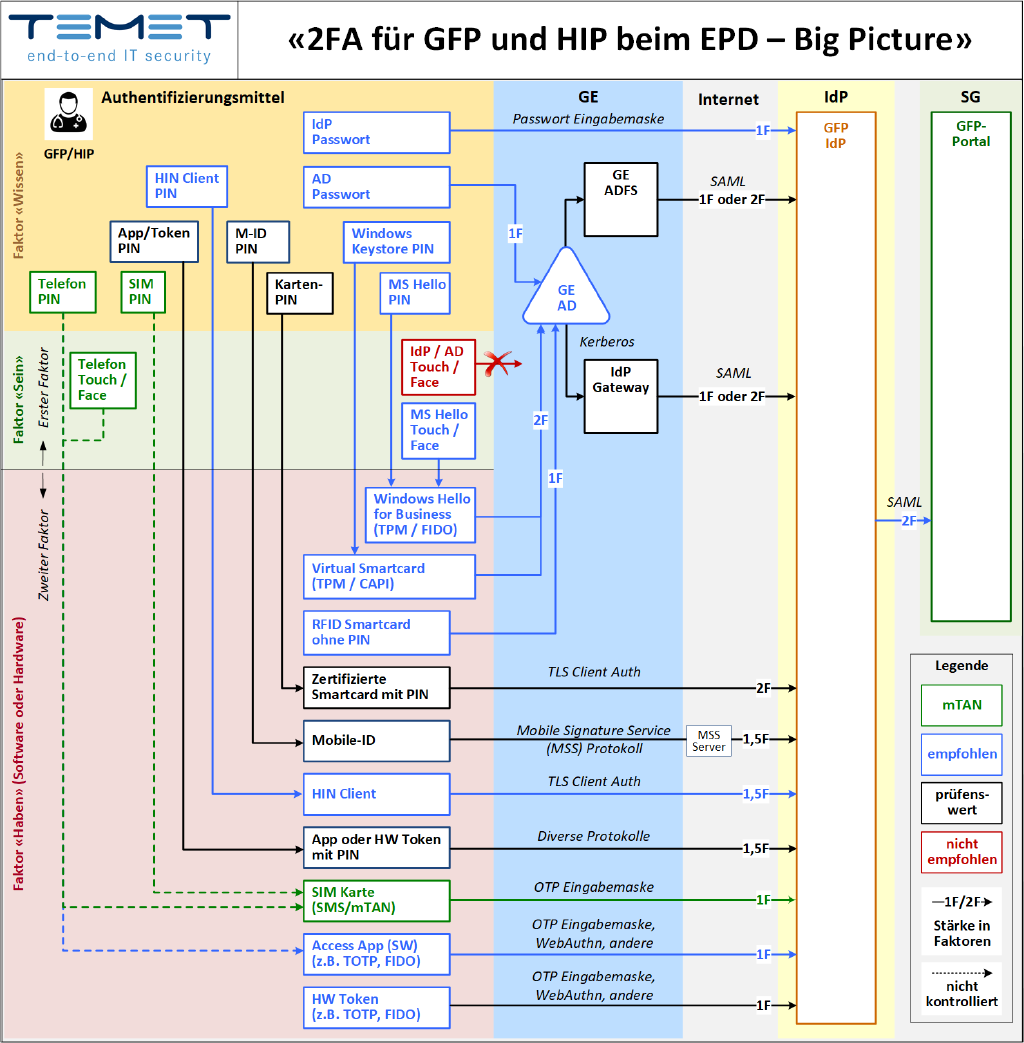
The diagram shows different variants for 2-factor authentication. A “have” factor (red area) is required in all cases and is combined with either a “know” factor (yellow area) or a “being” factor (green area). Authentication to the identity provider (IdP) is carried out either directly or via the Active Directory of the healthcare facility (GE AD)._
The following solutions are particularly interesting:
- Still very common today is the so-called mTAN procedure, which combines a password (“know” factor) with a SIM card (“have” factor), whereby possession of the SIM card is verified by the delivery of a one-time password via SMS. The mTAN procedure is particularly interesting when logging on to the Windows workstation with the Active Directory password as the first factor. However, due to the increasing number of attacks on cell phones and GSM networks, the mTAN procedure has passed its zenith.
- In today’s “mobile first” era, a wide variety of authentication apps are fighting for market share. In addition to the products of the big players such as “Google Authenticator” or “Microsoft Authenticator”, niche providers such as Kobil, Vasco or Futurae have also been able to establish themselves with interesting products. It is not possible at this point to go into the various versions of these apps in terms of communication protocols and user interactions as well as the use of the numerous sensors available on the smartphone.
- What all authentication apps have in common is the threat posed by malware that can be installed on the app’s carrier device. Providers of hardware tokens are therefore using the argument of malware resistance. Easy-to-use FIDO tokens such as Yubikey or Google Titan are also creating innovative movement in this market segment. The Mobile ID offered by Swisscom, Sunrise and Salt is based on the SIM card and can also be categorized as a hardware token.
- The FIDO 2 standard is also the basis of Windows Hello for Business, with which Microsoft wants to fulfill the promise of password-free authentication. This method combines the possession of a secure hardware component (“having” factor: a Trusted Platform Module; TPM) installed in the end device with either a biometric pattern (“being” factor: fingerprint or facial recognition) or with a PIN (“knowing” factor) and offers 2-factor authentication to the company’s internal Active Directory or to the Azure Active Directory in the cloud. It should be noted that biometric patterns should only be stored decentrally in personal hardware and cross-checked. Biometric procedures do not enable FA on their own, but are definitely interesting in combination with a “credit factor”, especially as the quality of modern sensors can certainly compete with the quality of a typical PIN.
Three directions for the 2FA of CFP and HIP
Given the current state of the art, we recommend aiming for a different solution for each of the following three use cases:
- A solution with minimal investment on the part of healthcare institutions, based on the combination of the Active Directory password with an authentication app or hardware token. If both a token and an app are offered, users with and without smartphones can be optimally served. There is a wide range of products to choose from for both solution elements, whereby usability in everyday clinical practice should be considered as an important evaluation criterion.
- A maximally user-friendly solution** with single sign-on in the home or hospital, based on 2-factor authentication against the internal Active Directory, whereby the “rules of the game” for connecting an EPDG-certified identity provider (IdP) and its requirements for the internal components and processes must be clarified in advance and agreed with the regulator. Here too, there are various solutions such as Windows Hello for Business, Microsoft Virtual Smartcard or solutions with RFID smartcards.
- A solution specifically for healthcare professionals in private practice** that places the lowest possible demands on the user infrastructure and does not require a local authentication system.
The modern development of IT (keyword “cloud”) will lead to more and more services being obtained from the Internet. As a result, 2FA-secured access in the form of the EPD will sooner or later become the norm. It is therefore important to set the right course today and invest in an expandable solution for 2-factor authentication for the EPR.
Note: This article was also published in the magazine HEIME & SPITÄLER 1 | MÄRZ 2019.
Security Architecure Strong Authentication

